In the modern digital age, cybersecurity courses is an essential component of every organization’s infrastructure. With the rising frequency of cyberattacks, the demand for cybersecurity professionals is higher than ever. The risks posed by hackers and cybercriminals have forced businesses to focus heavily on strengthening their digital security measures. As a result, professionals with skills in protecting sensitive data and securing networks are in high demand.
For anyone looking to break into the cybersecurity industry or elevate their career to new heights, choosing the right course is critical. The right training can lead to a rewarding career path with excellent job opportunities, competitive salaries, and the chance to make a meaningful impact in the digital world.
At Elysium Academy, we offer specialized, hands-on cybersecurity courses designed to prepare you for the future of cybersecurity. These courses are taught by industry professionals and provide you with the tools needed to become a sought-after cybersecurity expert. Let’s dive into the top 8 high-impact cybersecurity courses that will help you carve out your place in this thriving field.
Ethical Hacking and Penetration Testing
Ethical hacking and penetration testing are pivotal in today’s cybersecurity landscape. Ethical hackers are tasked with identifying weaknesses in a system or network before malicious hackers can exploit them. This course is not only about finding vulnerabilities but also understanding how to prevent them and ensure system security.
Key Learning Outcomes:
-
Penetration Testing: Learn the practical aspects of conducting penetration tests on various systems, from web applications to networks and databases.
-
Vulnerability Assessments: Master the process of identifying and assessing security weaknesses across different platforms.
-
Tools and Techniques: Gain experience with essential tools like Metasploit, Nmap, and Wireshark, which are critical for carrying out penetration tests.
Why Choose This Cybersecurity Courses?
Ethical hackers are vital in the fight against cybercrime. By pursuing this course, you’ll acquire the skills needed to prevent data breaches, secure networks, and safeguard critical infrastructure. Ethical hacking offers one of the most exciting and fast-paced career paths in cybersecurity.
Certified Information Systems Security Professional (CISSP)
The CISSP certification is designed for experienced cybersecurity professionals looking to step into leadership roles. This course goes beyond technical skills to include management, risk assessment, and governance, ensuring you understand how to create comprehensive security frameworks for organizations.
Key Learning Outcomes:
-
Security & Risk Management: Learn to assess and manage risks, crucial for safeguarding an organization’s entire infrastructure.
-
Security Architecture and Engineering: Gain expertise in designing and implementing security architectures tailored to organizational needs.
-
Communication and Business Skills: Learn how to align IT security measures with business goals and communicate effectively with stakeholders.
Why Choose This Cybersecurity Courses?
CISSP is recognized globally as one of the most prestigious certifications in cybersecurity. Professionals who earn this certification are equipped to lead security efforts at an organizational level and are often sought after for CISO or Security Architect roles.
Certified Ethical Hacker (CEH)
The Certified Ethical Hacker (CEH) course is one of the most recognized in the cybersecurity world. It trains professionals to think like hackers to better protect systems and networks from malicious attacks. This course provides practical knowledge on how to exploit vulnerabilities ethically.
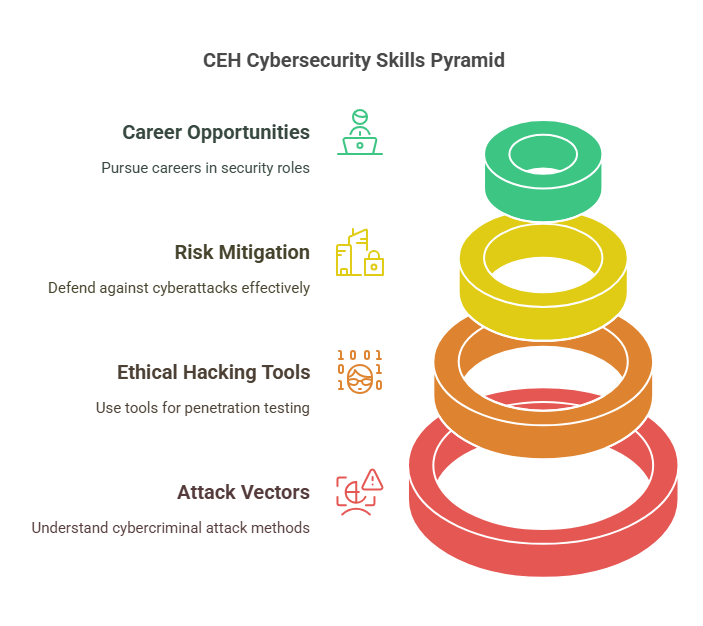
Key Learning Outcomes:
-
Attack Vectors: Understand the different types of attack vectors used by cybercriminals, including malware, social engineering, and DoS attacks.
-
Ethical Hacking Tools: Learn to use tools like Kali Linux, Nmap, and Burp Suite to perform penetration tests and simulate attacks.
-
Risk Mitigation: Learn strategies to defend against cyberattacks and strengthen security defenses across networks and systems.
Why Choose This Cybersecurity Courses?
CEH is an excellent certification for those who want to pursue a career in penetration testing, network security, or ethical hacking. By learning to think like a hacker, you’ll gain a deeper understanding of how to anticipate and prevent potential security breaches.
CompTIA Security+
CompTIA Security+ is a fundamental course that covers essential concepts in network security and is an excellent starting point for beginners entering the cybersecurity field. It provides a solid foundation in how to protect networks and systems from cyber threats.
Key Learning Outcomes:
-
Cryptography and PKI: Learn how encryption and public key infrastructure help protect sensitive data and communications.
-
Network Security: Understand how to secure network infrastructures and prevent unauthorized access.
-
Compliance and Operational Security: Get to grips with security policies, compliance standards (e.g., GDPR), and the operational aspects of maintaining a secure network.
Why Choose This Cybersecurity Courses?
Security+ is perfect for newcomers to cybersecurity, as it offers broad coverage of topics and serves as a stepping stone to advanced certifications. It’s one of the most popular entry-level cybersecurity certifications and is recognized globally.
Certified Information Security Manager (CISM)
CISM focuses on the management aspects of cybersecurity, offering training in designing and overseeing security policies and procedures. It’s intended for professionals who want to move into roles involving the strategic direction of security efforts within an organization.
Key Learning Outcomes:
-
Security Governance: Learn to develop and implement security policies that align with business objectives and ensure compliance.
-
Incident Response: Gain the skills to manage and mitigate security incidents, ensuring rapid recovery and minimal damage.
-
Risk Management: Learn to identify, assess, and manage cybersecurity risks effectively.
Why Choose This Cybersecurity Courses?
CISM is tailored for those aiming for high-level positions like Security Manager or Chief Information Security Officer (CISO). It provides essential skills for handling the strategic and operational components of an organization’s security.
Network Security and Firewalls
Securing network infrastructures is one of the primary responsibilities of cybersecurity professionals. This security course focuses on the techniques and tools needed to protect networks from cyberattacks using firewalls, intrusion detection/prevention systems (IDS/IPS), and more.
Key Learning Outcomes:
-
Firewall Configuration: Learn how to install and configure firewalls to monitor and filter incoming and outgoing network traffic.
-
Intrusion Detection Systems (IDS): Gain insights into IDS/IPS tools and techniques for identifying and preventing unauthorized access.
-
Secure Network Architecture: Learn how to build and maintain a secure network, integrating various layers of security.
Why Choose This Cybersecurity Courses?
With businesses increasingly dependent on network infrastructures, network security experts are essential for safeguarding sensitive data from external threats. This course is ideal for those pursuing careers in network security or system administration.
Cloud Security
As more organizations adopt cloud technologies, the need for cloud security experts has skyrocketed. This course focuses on the unique challenges and solutions associated with securing cloud environments, from private to hybrid and public clouds.

Key Learning Outcomes:
-
Cloud Security Frameworks: Learn about global cloud security frameworks such as ISO 27001, CSA STAR, and others.
-
Securing Cloud Applications: Understand the best practices for securing cloud-based applications, services, and data.
-
Cloud Compliance: Learn how to maintain compliance with cloud security standards and regulations.
Why Choose This Cybersecurity Courses?
Cloud security is a rapidly growing field, and as organizations migrate their data to the cloud, the need for specialized experts in cloud security is immense. This course prepares you to handle the complexities of securing cloud-based systems.
Cybersecurity Risk Management
Cybersecurity risk management is the process of identifying, assessing, and mitigating risks to an organization’s IT infrastructure. This course focuses on building a solid understanding of how to manage cybersecurity risks across the entire organization.
Key Learning Outcomes:
-
Risk Assessment: Learn how to conduct thorough risk assessments, identifying potential threats and vulnerabilities.
-
Risk Mitigation Strategies: Develop strategies to minimize risks through security controls and countermeasures.
-
Incident Response and Recovery: Learn how to prepare for and respond to cybersecurity incidents effectively.
Why Choose This Cybersecurity Courses?
Effective risk management is crucial for any organization. By taking this course, you will learn to protect your company’s assets and ensure its long-term cybersecurity success.
Tabular Column: Key Details of the Cybersecurity Courses
| Course Name | Level | Duration | Prerequisites | Key Certifications |
|---|---|---|---|---|
| Ethical Hacking and Penetration Testing | Intermediate | 4-6 weeks | Basic knowledge of networks and OS | None |
| CISSP | Advanced | 6-8 weeks | 5 years of work experience in security | CISSP |
| Certified Ethical Hacker (CEH) | Intermediate | 4-6 weeks | Basic networking knowledge | CEH |
| CompTIA Security+ | Beginner | 3-4 weeks | None | CompTIA Security+ |
| Certified Information Security Manager (CISM) | Advanced | 8-10 weeks | 5 years of security work experience | CISM |
| Network Security and Firewalls | Intermediate | 4-6 weeks | Knowledge of networking | None |
| Cloud Security | Advanced | 4-6 weeks | Experience with cloud technologies | None |
| Cybersecurity Risk Management | Intermediate | 4-6 weeks | Basic knowledge of IT infrastructure | None |
FAQs
1. What career options are available after completing a cybersecurity courses?
After completing a cybersecurity courses, you can explore roles such as Security Analyst, Ethical Hacker, Penetration Tester, Security Consultant, Network Engineer, Cloud Security Engineer, and more.
2. Are these courses suitable for beginners?
Yes, several courses, like CompTIA Security+ and Ethical Hacking, are designed to cater to beginners. However, some advanced courses require prior experience in IT and networking.
3. How long does it take to complete a cybersecurity course?
The duration varies depending on the course, but typically ranges from 3 to 10 weeks.
4. What is the job market like for cybersecurity professionals?
The job market is booming. Cybersecurity professionals are in high demand globally, with numerous opportunities across all industries, particularly in sectors like finance, healthcare, and technology.
5. Can I pursue a career in cybersecurity without a technical background?
Yes! Many cybersecurity courses are designed to be beginner-friendly, and with dedication and practice, you can enter the field even without a technical background.
Final Thoughts
The digital world is vast, and with it comes a complex landscape of cyber threats. To stay ahead of these risks and make meaningful contributions to digital security, it’s essential to pursue relevant, high-impact cybersecurity training. At Elysium Academy, we offer courses that equip you with the necessary skills and certifications to thrive in the evolving field of cybersecurity.
By selecting the right Cybersecurity Courses, you’ll not only enhance your knowledge but also significantly boost your employability and career prospects in cybersecurity. From ethical hacking to cloud security, these high-demand courses pave the way for a rewarding and impactful career.
So why wait? Choose the right Cybersecurity Courses, start learning, and take your first step towards becoming a cybersecurity expert with Elysium Academy.













